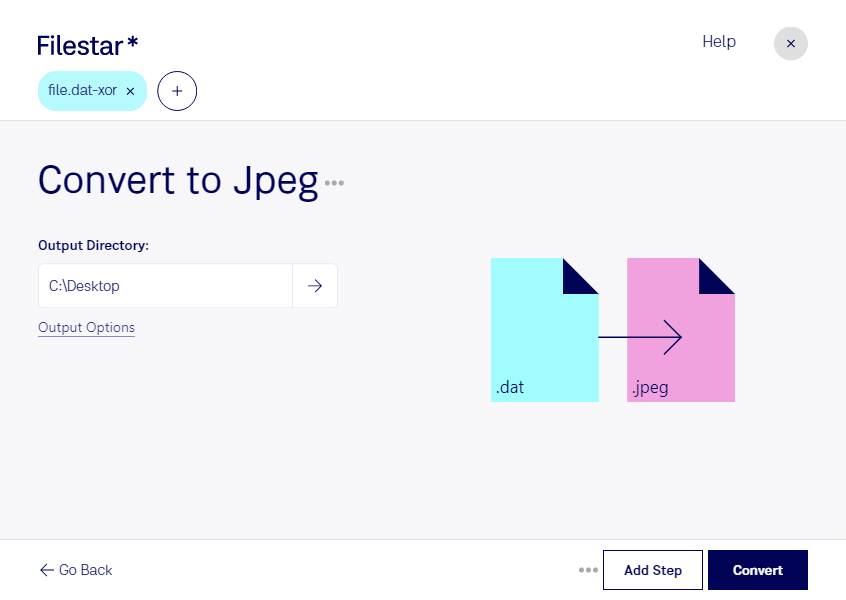
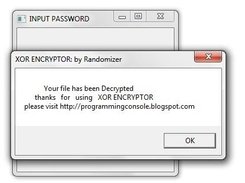
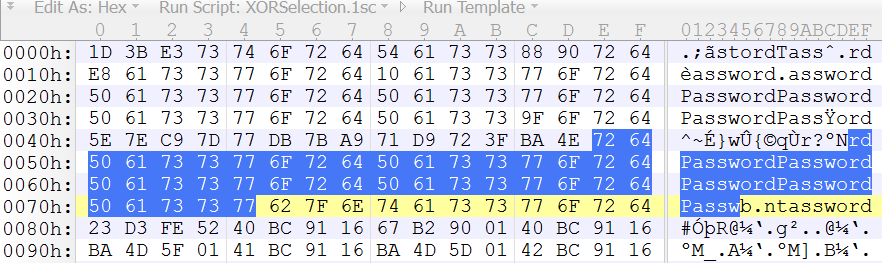
XOR operation on a file The file restoration process is the opposite of... | Download Scientific Diagram
Xor Download: A very lightweight command-line application that will make it possible for everyone to scramble and encrypt any file using a special key
GitHub - mightbesimon/XOR-file-encryption: Encrypts files with a password byte-by-byte using a XOR cipher

XOR operation on a file The file restoration process is the opposite of... | Download Scientific Diagram
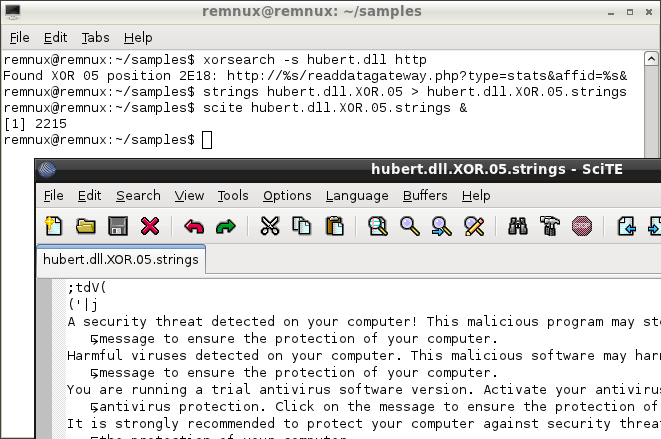
![1.3.4 Multi-byte XOR Encoding - Learning Malware Analysis [Book] 1.3.4 Multi-byte XOR Encoding - Learning Malware Analysis [Book]](https://www.oreilly.com/api/v2/epubs/9781788392501/files/assets/ea8a8dd5-0eab-43a6-a32c-83a82f4759dc.png)